Trace features
Ozone is more than a simple debugger, it is a performance analyzer that offers trace features for deep-insight system analysis.

With direct integration of J-Trace, Ozone enables CPU instruction trace and offers different possibilities to analyze the run-time behavior and performance of a target system. Instruction trace enables full system insight, far more than what is possible with simple debugging and printf-style output.
Ozone's trace-related windows provide multiple ways and views to find bugs and inefficiencies and to verify that a system behaves as expected.
Tracing does not have to require any target code modification or huge setup. Get up and running in less than 15 minutes with Ozone and J-Trace PRO.
Instruction Trace
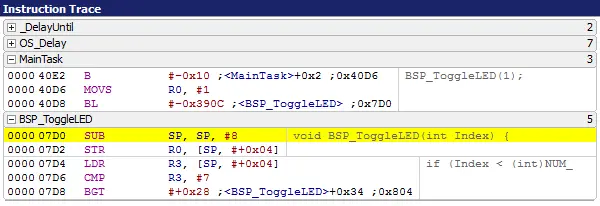
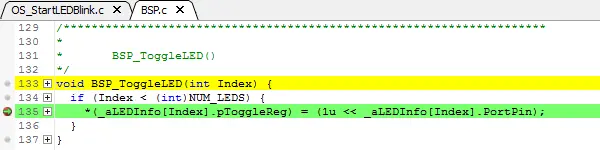
The basic information provided by trace data is the instruction trace. When the target is halted, Ozone shows the most recently executed instruction in its Instruction Trace Window. This allows you to analyze what your system did last.
Code Coverage
The trace capability can provide accurate information about the instruction execution on the target system. This enables a full code coverage analysis of the system which can be updated while the target is running.
Code Profiling
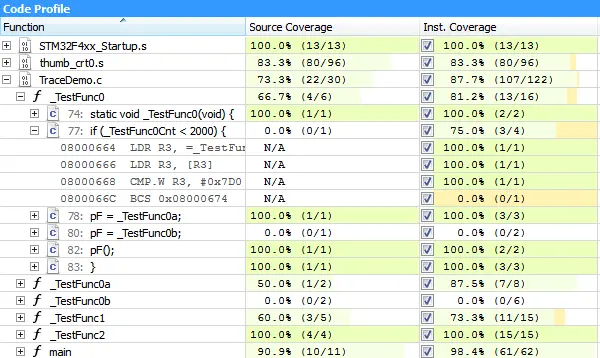
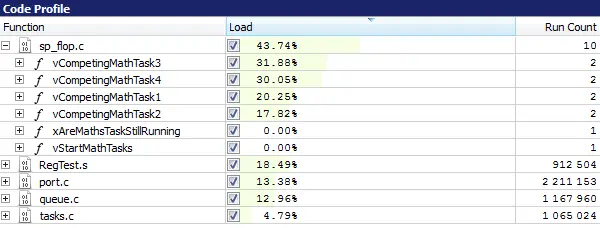
With the J-Trace PRO streaming trace capabilities, trace data is analyzed in real-time, while the data is transferred from the target system to the host computer. The analyzed data contains information about which instructions have been executed on the target, whether conditional instructions have taken both paths, and how often each instruction has been executed. With the captured trace data, Ozone analyzes your application to construct a code profile and identify "hot spots" for potential optimization.
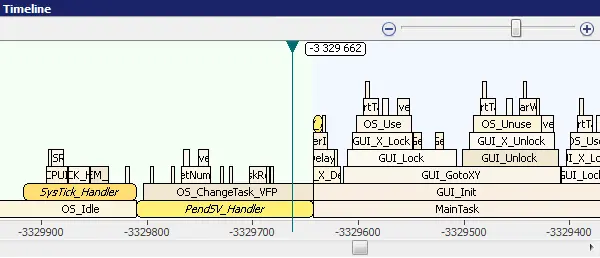
Timeline
The Timeline Window provides a graphical representation of the Call Stack over time. The timeline is based on the recorded trace data, mapped to the source function information.
Each call frame of the timeline stack resembles a function invocation. With the timeline you can easily measure how long a function call took, which sub-routines have been called, and how much time has been spent in sub-routines. Discontinuities in program flow, for instance interrupts and context switches, are highlighted with a background color change to enable you to easily identify these highly significant events.
With OS awareness, the Timeline Window supports identification of task switches to restart the call stack. You can now see when task switches happen and which function calls belong to a task execution. Without OS awareness, the functions might endlessly stack when Ozone does not know where task switches happen.
The Timeline Window is synchronized with the Instruction Trace Window to allow fast navigation in your application flow and immediate identification of what you are currently looking at.
Requirements
The trace features can be used when the target system supports CPU trace. There are two trace methods:
Trace Pins
A J-Trace is connected to the trace pins of the target device. All trace data generated by the Embedded Trace Macrocell (ETM) is sent on these pins and recorded by J-Trace. With a J-Trace PRO the trace data is immediately sent to the host PC, which enables unlimited recording of the target execution and provides full system insight. With an older J-Trace the trace data is stored in a 64 MB internal buffer and the latest trace data, usually about the last 2 seconds of execution, is read by the PC when the target is halted.
Trace Buffer
If the target device includes an Embedded Trace Buffer (ETB) or similar, trace can be done with a J-Link. The trace data is then written by the target into the internal trace buffer of usually about a few kilobytes and read by J-Link when the target is halted. With a trace buffer the last few thousand executed instructions can be available, which does not provide full insight, but can be useful to recall the execution flow before a fault or issue occurs.