Security consideration
Security Consideration
If you want to check the integrity of your data, for instance the firmware running on your product, you would normally include a checksum or hash value into it, generated by a CRC or SHA function. Hashes are excellent at ensuring a critical data transmission, such as a firmware download, has worked flawlessly and to verify that an image, stored in memory, has not changed. However they do not add much security, as an attacker can easily compute the hash value of modified data or images. Digital signatures can do more. In addition to the integrity check, which is provided by hash functions, a digital signature assures the authenticity of the provider of the signed data, as only he can create a valid signature. emSecure comes in different versions with different digital signature algorithms to fit any requirements of size or speed.
emSecure can be used for two security approaches:
1. Anti-hacking: Prevent tampering or exchange of data, for example the firmware running on a product, with non-authorized data.
2. Anti-cloning: Prevent a firmware to be run on a cloned hardware device.
Anti-Hacking — Authentication of Firmware
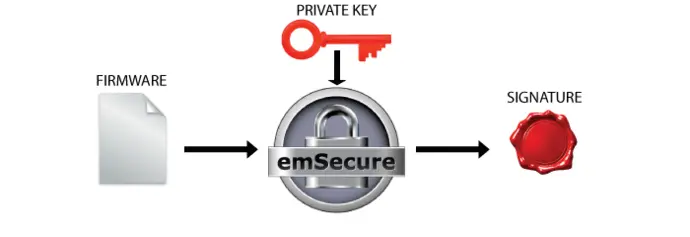
Firmware Signing in Production
To make sure only authorized firmware images are run on a product the firmware image will be signed with emSecure. To do this an emSecure key pair is generated one time. The private key will be included in the production process of the firmware. Once a firmware is created and ready to be shipped or included into a product it will be signed with this private key. The signature will be transferred and stored in the product alongside the firmware.
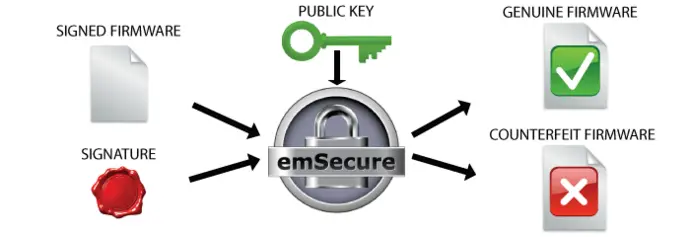
Anti-Hacking Bootloader Verification
The public key will be included in the bootloader of the product, which manages firmware updates and starts the firmware.
On a firmware update and when starting the product, the bootloader will verify the firmware by its signature. If they match, the firmware is started, otherwise the application will stay in the bootloader or even erase the firmware.
Anti-Cloning — Authentication of Hardware
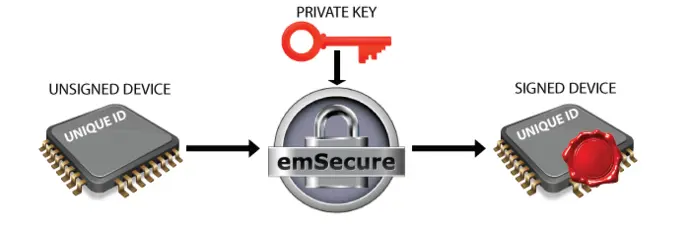
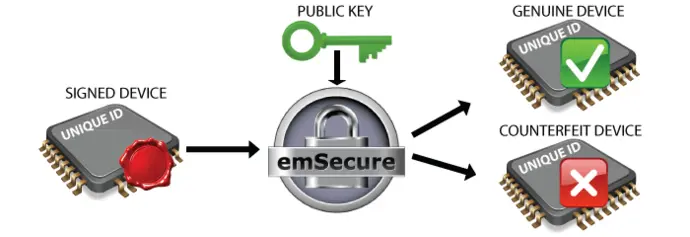
Anti-Cloning Firmware Verification
The private key will be included in the production process of the product. At the end of the production process, after the unit is assembled and tested, some hardware-specific, fixed, and unique data, like the unique id of the microcontroller is read from the unit. This data is signed by emSecure with the private key and the signature is written back to the unit into an OTP area or a specified location on memory. The public key will be included in the firmware which will run on the product. When the firmware is running it will read the unique data from the unit and verify it with the signature. When the signature does not match, for example, when it was simply copied to a counterfeit unit with other unique data, the firmware will refuse to run.