Target Encrypted Link Package (TELP)
Protecting intellectual property with secure programming
As an option to SEGGER's secure programming solution – the combination of Flasher Secure and Flasher Secure Server – SEGGER's Target Encrypted Link Package (TELP) enables the programming of any microcontroller using encrypted end-to-end communication.
Overview
Developed by SEGGER and used by numerous well-known customers, TELP is SEGGER's secure programming package for the encrypted transfer of firmware to a microcontroller. Using the Target Encrypted Link Package in addition to SEGGER's secure programming solution consisting of Flasher Secure and Flasher Secure Server, and optionally emSecure, SEGGER's anti-cloning software, enables highly secure programming.
Key features
SEGGER's Target Encrypted Link Package (TELP) delivers cutting-edge security for firmware programming, ensuring the safe transfer of intellectual property to microcontrollers. Designed to meet diverse needs, TELP provides robust protection against eavesdropping, supports microcontrollers with minimal hardware requirements, and functions seamlessly even on devices without built-in security features. These key capabilities make TELP a trusted solution for secure production environments.
Protection of intellectual property against eavesdropping
TELP ensures that intellectual property remains secure during firmware programming by encrypting communication and blocking unauthorized access. This protection prevents eavesdropping, firmware leaks, and hardware cloning.
Support for any microcontroller with minimal memory configuration
TELP works with microcontrollers that have basic Flash read protection and minimal memory requirements, needing only 8 KB of flash and RAM memory to implement its security features.
Compatibility with microcontrollers lacking security engines
TELP is versatile and functions with microcontrollers even if they lack a dedicated security engine, enabling encrypted programming and secure communication regardless of hardware constraints.
Use cases
When it comes to manufacturing, the protection of intellectual property (IP) is of paramount concern for both IP owners and contract manufacturers. Using SEGGER's Target Encrypted Link Package (TELP), both parties can find peace of mind, knowing that intellectual property remains secure during production processes. Using TELP ensures that only IP owners have full access to their IP.
Contract manufacturers
As a contract manufacturer, your customers' trust is critical. They need to know that their firmware is in safe hands. This means no firmware leaks, no cloned hardware devices, no eavesdropping. To provide a highly secure production environment, TELP is the right choice. Combined with the Flasher Secure, it ensures that your customers' intellectual property is secure at every stage of production.

IP owners
As an intellectual property owner, protecting your innovations and ideas from unauthorized access and replication by third parties is critical. Addressing these concerns becomes even more complex when manufacturing processes take place at a third-party location, where maintaining the security of sensitive data during production is a top priority. TELP addresses these vulnerabilities while giving you full control over the programming process.
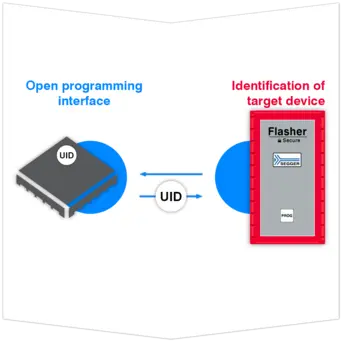
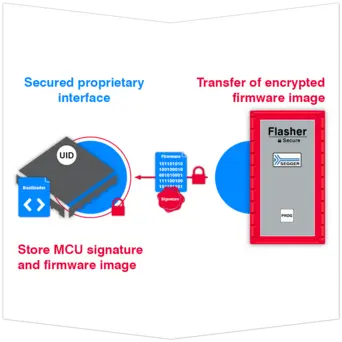
How TELP works
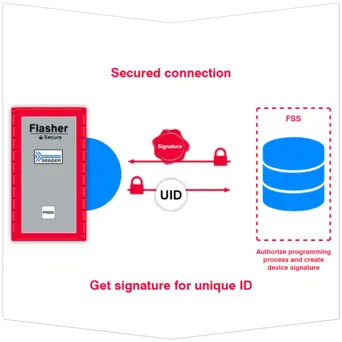
Using SEGGER's Flasher Secure Server when programming microcontrollers already reduces the risk of counterfeiting due to a data leak or IP loss and unauthorized production. SEGGER's TELP adds protection to the last few inches of communication, safeguarding the customer's target firmware against sniffing or dumping.
Even if all communication between the IP owner and the production device already is encrypted, there still is one last weak spot – the link between the programmer and the target memory (ISP). TELP ensures that even the last few inches of cable are protected from sniffing by encrypting the communication.
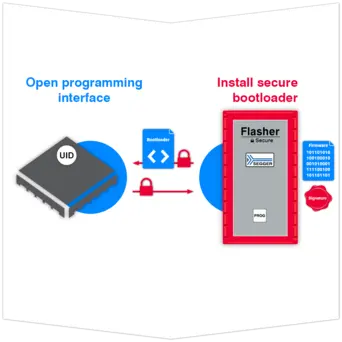
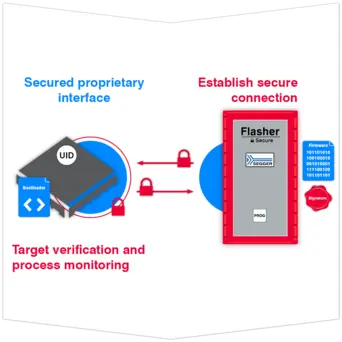
Establish secure connection
Once the Flasher Secure has established a secure connection with the MCU, a proprietary interface is opened between the Flasher Secure and the microcontroller. After installing the secure bootloader, communication with the processor can only occur through the interface established by the firmware between the Flasher Secure and the target device.
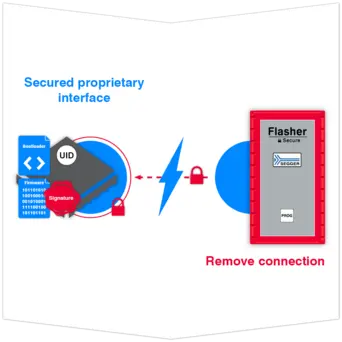
Decrypt and install firmware and remove secure bootloader
In the final step, the microcontroller itself decrypts and installs the firmware onto the microcontroller, subsequently removing the secure bootloader. Once this process is completed, the firmware becomes ready-to-run and it blocks unwanted access from external sources.
Requirements
Using SEGGER's Target Encrypted Link Package for secure programming requires:
- Flasher Secure Server (FSS)
- Flash programmer Flasher Secure
- Authentication via emSecure
- 8 KB of flash and RAM memory
- Flash read protection capability on the MCU
Get in touch with us
Have questions or need assistance? Our Embedded Experts are here to help!
Reach out to us for:
- Licensing quotes
- Technical inquiries
- Project support