emSecure-RSA
The default version of emSecure
emSecure-RSA is the default version of emSecure, based on RSA asymmetrical encryption.
Using emSecure-RSA
All emSecure products are created to be simple but powerful, and easy to integrate. It can be used in new products and even extend existing ones as emSecure is a software solution and no additional hardware is required. The code is completely written in ANSI C and can be used platform- and controller-independent. The required key pairs can be generated with the included tool. A pass-phrase can be used to regenerate the keys. The generated keys can be exported into different formats to be stored on the application code or loaded from a key file. This allows portability and exchangeability between different platforms. Signing data, for instance firmware images, can be performed with the included tool. It is also possible to integrate the signing process directly into a production application running on any PC or even on a microcontroller. Once a signature is generated, the signed data can be verified by its signature in an embedded application or on an external application communicating with the device. Verifying data takes less than 20 ms on a STM32F746, running at 216 MHz, which is not significantly more time for a bootloader to start firmware.
Performance
emSecure-RSA aims for portability and is designed to fit speed and size requirements for different targets. The process of verifying data is technically split up into two steps:
- Compute the hash of the data.
- Decrypt the signature and compare the hash values.
Step 1, the computation of the hash, depends on the size of the data, whereas step 2 is dependent on the key length and takes the same time to verify any data.
| Step | Performance |
|---|---|
| Compute the hash of the data | |
SHA-1 | 12.5 MB/sec |
| Decrypt the signature and compare the hash values | |
| RSA 512 bit Signature decryption and verification | 0.84 ms |
| RSA 1024 bit Signature decryption and verification | 2.15 ms |
| RSA 2048 bit Signature decryption and verification | 7.29 ms |
| RSA 512 bit Signature generation and encryption | 13.95 ms |
| RSA 1024 bit Signature generation and encryption | 63.60 ms |
| RSA 2048 bit Signature generation and encryption | 362.75 ms |
Test configuration
- SEGGER Embedded Studio 3.35 using clang 5.0.1 compiler
- SHA-1 algorithm configured for speed optimization
- Test on a STM32F746 microcontroller, running at 216 MHz
Verifying Data
The following table shows some total values to verify different amounts of data.
| Data size | Key length | Decryption and verification | Hash computation | Total time |
|---|---|---|---|---|
| 1 kByte | 512 bit | 0.84 ms | 0.09 ms | 0.93 ms |
| 100 kByte | 512 bit | 0.84 ms | 7.35 ms | 8.19 ms |
| 1 kByte | 1024 bit | 2.15 ms | 0.09 ms | 2.24 ms |
| 100 kByte | 1024 bit | 2.15 ms | 7.35 ms | 9.50 ms |
| 1 kByte | 2048 bit | 7.29 ms | 0.09 ms | 7.38 ms |
| 100 kByte | 2048 bit | 7.29 ms | 7.35 ms | 14.64 ms |
Signing Data
The following table shows some total values to sign different amounts of data.
| Data size | Key length | Decryption and verification | Hash computation | Total time |
|---|---|---|---|---|
| 1 kByte | 512 bit | 13.95 ms | 0.09 ms | 14.04 ms |
| 100 kByte | 512 bit | 13.95 ms | 7.35 ms | 21.30 ms |
| 1 kByte | 1024 bit | 63.60 ms | 0.09 ms | 63.69 ms |
| 100 kByte | 1024 bit | 63.60 ms | 7.35 ms | 70.95 ms |
| 1 kByte | 2048 bit | 362.75 ms | 0.09 ms | 362.84 ms |
| 100 kByte | 2048 bit | 362.75 ms | 7.35 ms | 370.10 ms |
Memory Footprint
The following table lists the memory requirements of emSecure-RSA configured for operation with a 2048 bit key.
| ROM | Static RAM | Stack | |
|---|---|---|---|
| Sign only | 5.81 KB | 0.03 KB | 2.12 KB |
| Verify only | 4.88 KB | 0.03 KB | 2.93 KB |
| Sign and verify | 6.35 KB | 0.03 KB | 2.93 KB |
Test configuration
- SEGGER Embedded Studio 3.35 using GCC compiler
- SHA-1 algorithm configured for size optimization
- Compiled for Thumb-2 instruction set, optimized for size
Included Sign and Verify Applications
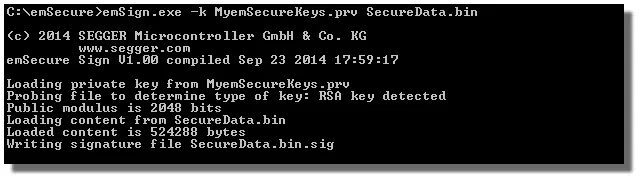
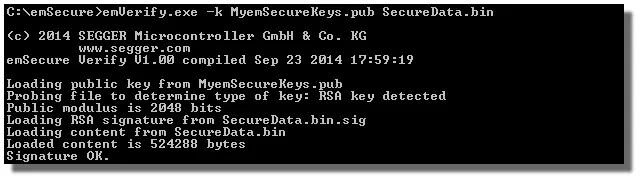
emSecure includes all basic applications needed for securing a product. The applications' source-code is included and provides an easy to use starting point for modifications and integration into other applications.
The sign and verify applications are also available for evaluation. For more information contact us at info@segger.com
| Application name | Target platform | Description |
|---|---|---|
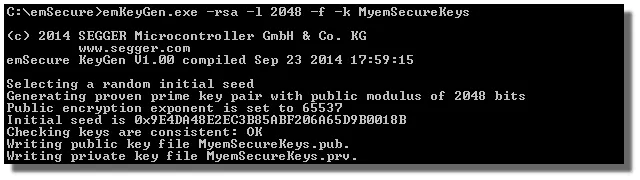
| emKeyGen | Windows | Generates a key pair with a given key length, either random or from a given seed. |
| emSign | Windows | Digitally signs a file with your private key. |
| emVerify | Windows | Verifies the signature of a digital asset with its public key. |
| emPrintKey | Windows | Exports keys and signatures into C source format, to be included into any application. |
The utilities are PC applications, ready-to-use for the setup step to secure your product.
Key Generation: emKeyGen generates a public and a private key. The generation parameters can be set with command line options. The keys are saved in a common key file format and can be published and exchanged.
Technical Background
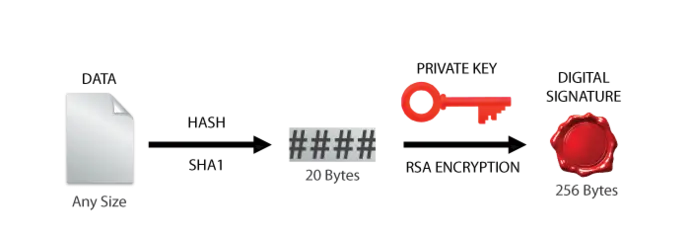
emSecure Verification Technical Details: The emSecure-RSA verification process starts with the data one wishes to verify and the digital signature which was created from the original file. A hash file is generated for the unverified data. The public key and RSA decryption is used to generate the original hash and then compared to verify whether the data file is genuine.